Qian Cui
PhD StudentUniversity of Ottawa Big fan of Linux and embedded system


2016-Now
University of Ottawa, Ottawa
PhD of Computer Science
2007-2009
BeiHang University, Beijing
Master of Computer Architecture in Computer Science
2003-2007
BeiHang University, Beijing
Undergraduate Degree in Computer Science
2013-2015
Samsung Electronics, Beijing
Embedded Engineer
2009-2012
Space Star Co. Ltd, Beijing
FPGA Engineer
2011
CN 101969358A
A high-speed parallel architecture for RS decoding
Link for this work
2012
CN 102361460A
A high-speed parallel architecture for Viterbi decoding
Link for this work
2013
CN 102708012B
A fault-tolerant and parallel computing system of satellite
Link for this work
2014
CN 103678206A
A remote sensing data processing system based on FPGA
Link for this work
Qian Cui, Guy-Vincent Jourdan, Gregor v. Bochmann, Russell Couturier, Iosif-Viorel Onut.
Tracking Phishing Attacks Over Time.
26th International World Wide Web Conference(WWW '17), 2017
Paper Link
Qian Cui, Xiaopeng Gao, Xiang Long.
Design and Implementation of PCI Express DMA Controller Based on Weighted Round Robin Policy (in Chinese)
.Microcomputer Information, 2010, 26(23):147-149.
Zhe Zhang, Qian Cui, Xiaopeng Gao, Xiang Long.
Network Application for Multi-Core Architecture (in Chinese)
.Microelectronics & Computer, 2007, 24(10):39-42.
Over 50,000 Lines:
C/Python/Shell
Over 10,000 Lines:
Verilog/Java
Swimming/Traveling/Photography/Table Tennis
Phishing sites detection and track the phishing attacks
· Although the number of phishing attacks is increasing over time, we find that few new attacks are created, instead, most of the attacks are the variation or duplications of another one. Based on such observation, we build a phishing fingerprint database covering more than 50,000 phishing attacks, and detect new phishing variations through the similarity comparison of footprint. The result shows that such method could detect more than 90% phishing variations
· Through exploring the servers hosting the phishing attacks, in some cases, we could collect the source code of phishing kits (the tool used to create phishing site). We use fuzzy hash to analyze the source code, and find many common code snippets. We are working on piecing together these code snippets to retrieve the creator fingerprint based on the programing style
· We also monitor the phishing activities over time, and try to find the activity patterns, like geographic pattern or target pattern, to uncover the phishing activity tail
Shopping assistant
· To help myself know when it's the best time to purchase my coveted items, I developed a crawler to track the price over different shopping sites, and find the best timing for purchasing
wiGig wireless Linux driver and software architecture
· This project is to develop an effective driver for Samsung high speed WiFi chip
· Optimize cache access efficiency during DMA operation
· Optimize DMA operation by pipelined DMA ring
· Optimize socket transmission for jumbo frames
· Get final throughput: 3.0Gbps in UDP, 2.5Gbps in TCP.
Link for this work
Kernel porting and power optimization for Samsung
Exynos 5410 chip (four A15 cores and four A7 cores)
· Port kernel and uboot to Exynos 5410 chip
· Real-time optimize the network performance through monitoring the traffic
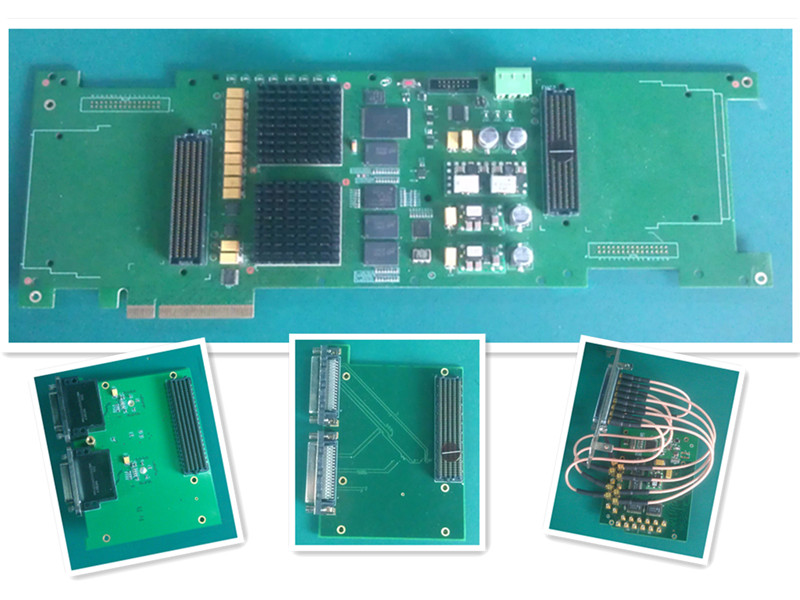
High-Speed prototype system based on PCI/PCI-E bus
· See the hardware section
Optimization Viterbi and RS decoding algorithm
· Implement Viterbi decoding parallel architecture based on Ping-
Pong buffering strategy
· Implement RS decoding parallel architecture based on interleaving dividing strategy
863 project “Reconstruction Accelerator”
· Design a duplex mode memory controller based on fair schedule strategy
· Design a parallel architecture for PSDM (Prestack Depth Migration) algorithm
Wormhole Router on SOC
· Design a new network modeling tool DClick for network on chip
Here are some my hardware designs when I was an FPGA engineer ^_^


My wife and I are keen to traveling and photography, here are some big gains during our tours.




